Encryption_analog
Overview
| Name | Type | Key Length | Additional info |
|---|---|---|---|
| Caesar Cipher | Monoalphabetic | Single digit | rot13 ftw |
| Simple Substitution | Monoalphabetic | 26 letters | Easily broken |
| Autokey Cipher | Polyalphabetic | Code word / phrase | Uses tabula recta |
| Running Key | Polyalphabetic | Book | Uses a paragraph from a book as key. |
| Chaocipher | Polyalphabetic | 52 letters | Uses disks that are modified according to a rule. |
Non-moving parts
Monoalphabetic
Caesar ciphers
Caesar ciphers are the simplest kind of cipher. Replace every letter by the letter that comes X numbers after it, where X is your key. It is considered to be extremely unreliable, because brute forcing this cipher will take a maximum of 25 attempts. However, it is fine for very very short messages (under 8 or 9 letters.)
Say your secret number is 8.
| A | B | C | D | E | ... |
| 1 | 2 | 3 | 4 | 5 | ... |
| +8 | +8 | +8 | +8 | +8 | ... |
| 9 | 10 | 11 | 12 | 13 | ... |
| I | J | K | L | M | ... |
HELLO = 8-5-12-12-15
+ 9 = + 9
QNUUX = 17-14-21-21-24
- 8 = - 8
IFMMP = 9-6-13-13-16
Rot13
"rot #" is used to signify the offset between the plaintext and its corresponding cipher alphabet. It's an interesting form of the Caesar or shift cipher because it's symmetric (the same process is used for encryption and decryption).
ABCDEFGHIJKLM~NOPQRSTUVWXYZ
NOPQRSTUVWXYZ~ABCDEFGHIJKLM
^ the shift occurs at the
13th character
Tap code
This is another very old cipher.
| 0 | 1 | 2 | 3 | 4 | 5 |
|---|---|---|---|---|---|
| 1 | A | B | C | D | E |
| 2 | F | G | H | I/J | K |
| 3 | L | M | N | O | P |
| 4 | Q | R | S | T | U |
| 5 | V | W | X | Y | Z |
A number represents a value at (column, row).
plain : J E W S
cipher: 24-15-52-43
Simple substitution
Unlike the Caesar cipher, which uses a code alphabet that's simply a shifted version of the normal alphabet, simple substitution ciphers use a completely jumbled up code alphabet. It's suitable for very short messages, given that a unique ciphertext alphabet is used for every short message. However, it's also vulnerable to brute force attacks, as well as frequency analysis. To use it, simply look up what a letter's equivalent cipher letter is, and replace it. Decryption is done by reversing the process.
plain : abcdefghijklmnopqrstuvwxyz
cipher: tgmsfdlrzwvjeaqcubxhionykp
plaintext : hello world
ciphertext: rfjjq yqbjs
Polyalphabetic
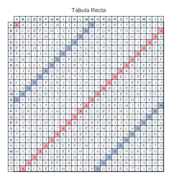
Tabula Recta
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
---------------------------------------------------
A A B C D E F G H I J K L M N O P Q R S T U V W X Y Z A
B B C D E F G H I J K L M N O P Q R S T U V W X Y Z A B
C C D E F G H I J K L M N O P Q R S T U V W X Y Z A B C
D D E F G H I J K L M N O P Q R S T U V W X Y Z A B C D
E E F G H I J K L M N O P Q R S T U V W X Y Z A B C D E
F F G H I J K L M N O P Q R S T U V W X Y Z A B C D E F
G G H I J K L M N O P Q R S T U V W X Y Z A B C D E F G
H H I J K L M N O P Q R S T U V W X Y Z A B C D E F G H
I I J K L M N O P Q R S T U V W X Y Z A B C D E F G H I
J J K L M N O P Q R S T U V W X Y Z A B C D E F G H I J
K K L M N O P Q R S T U V W X Y Z A B C D E F G H I J K
L L M N O P Q R S T U V W X Y Z A B C D E F G H I J K L
M M N O P Q R S T U V W X Y Z A B C D E F G H I J K L M
N N O P Q R S T U V W X Y Z A B C D E F G H I J K L M N
O O P Q R S T U V W X Y Z A B C D E F G H I J K L M N O
P P Q R S T U V W X Y Z A B C D E F G H I J K L M N O P
Q Q R S T U V W X Y Z A B C D E F G H I J K L M N O P Q
R R S T U V W X Y Z A B C D E F G H I J K L M N O P Q R
S S T U V W X Y Z A B C D E F G H I J K L M N O P Q R S
T T U V W X Y Z A B C D E F G H I J K L M N O P Q R S T
U U V W X Y Z A B C D E F G H I J K L M N O P Q R S T U
V V W X Y Z A B C D E F G H I J K L M N O P Q R S T U V
W W X Y Z A B C D E F G H I J K L M N O P Q R S T U V W
X X Y Z A B C D E F G H I J K L M N O P Q R S T U V W X
Y Y Z A B C D E F G H I J K L M N O P Q R S T U V W X Y
Z Z A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
---------------------------------------------------
A B C D E F G H I J K L M N O P Q R S T U V W X Y Z
Simple Polygraphic
A keyword is selected -- maybe "vigilance", or "ketchup", or "america", or what have you.
v i g i l a n c e v i g i l a n c e v i g i l a n c e v i
m e e t m e o n t u e s d a y e v e n i n g a t s e v e n
h m k b x e b p x p m y l l y r x i i q t o l t f g z z v
The keyword is repeatedly written above the message, and then the pair of letters (key letter + plaintext letter) are used to select a column and row. To decrypt the message, find the column that represents your key-letter, find the cipher-letter letter in the column, and see what letter your row represents.
Autokey
A key is written under the plaintext, followed by the plaintext, until the end of the message is reached. The plaintext letter and key letter are used as the X and Y coordinates in the tabula recta. Decryption follows a similar process, where one starts from the column of cipherletter, finds the key's letter in the column, and moves to the row's header to find the plaintext letter.
key: dqnboys
encryption:
plain : daddy cool died
key : dqnbo ysda ddyc
cipher: gqqem agrl glcf
decryption:
cipher: gqqem agrl glcf
key : dqnbo ys
plain : daddy co
Running Key
Rather than using a codeword, followed by the plaintext (the method of the autokey cipher), an external common source is used as the key. Ideally, this external source is as long as the message, or longer.
- For our first example, we'll use Genesis 1:1.
- For the next, we'll use the first post in the "bump this thread every day" thread on today's date.
plain : rip worldfourch and fuck mrvacbob
key : int hebeginning God crea tedthehe
cipher: zvi dsspjnbhzpn gbg hlgk fvytjfvf
cipher: ybgaezaihrwlvwoxueqoyqyoekvjmoirpljwslg
key : guyswhatdoiwoodturnonmylathetheressomeniceoak
A JavaScript tool can be useful for decryption.
Devices
Playing Cards
One of the most useful features of a playing card deck is that it can be used represent 2 different cipher alphabets. Shuffling a deck 7 or more cards provides a fairly random distribution of letters. Commonly, "red" is used for one alphabet, while "black" is used for the other. Jacks, Queens, and Kings represent 11, 12, and 13. Hearts & Spades refer to the letters A-M, while Clubs & Diamonds refer to the letters N-Z.
| ♠ Spades & Hearts ♥ | ♣ Clubs & Diamonds ♦ | ||
|---|---|---|---|
| A-B-C-D-E-F A-2-3-4-5-6 | G-H-I-J-K-L-M 7-8-9-10-J-Q-K | N-O-P-Q-R-S A-2-3-4-5-6 | T-U-V-W-X-Y-Z 7-8-9-10-J-Q-K |
SHCD = Spades, hearts, clubs, diamonds
deck order:
S4-D9-C4-CA-H9-D3-S6-C7-H5-C10-D5....
separated by color:
♠♣ S4-C4-CA-S6-C7-C10....
♥♦ D9-H9-D3-H5-D5....
♠♣ DQNFTW....
♥♦ VIPER....
Because a deck of playing cards only costs a few dollars and is commonly available, they can be an effective way of generating or delivering randomized alphabets.
Dice
Dice can be used to generate code words or code phrases. Roll four dice, and look up the numbers you rolled in the 4 dice table, or roll five dice, and use the EFF's long word list.
Codebooks
A code book consists of a series of numbers, each paired with a word or phrase. A number can also refer to a codeword or cipher alphabet, or a certain form of encryption.
Key Selection
- For simple substitution (which uses a scrambled alphabet):
- One can simply shift the standard alphabet (A-Z) by a number of places. (Caesar cipher)
- A word or phrase can begin the alphabet, followed by the rest of the alphabet. Remove duplicate letters.
- Eg: "DQNFTW" --> "DQNFTWABCEGHIJKLMOPRSUVXYZ"
- Eg: "buy vipcoins now" -> "buyvipconsw" -> "BUYVIPCONSWADEFGHJKLMQRTXZ"
- The alphabet can be jumbled up completely, either by a listing in a codebook, or by other methods.
Entropy:
- Two coin flips: 2
- Single dice: 2.6
- Single letter: 4.7
- Two dice: 5.2
- Two d20: 8.6
- Jumbled alphabet: 88.4
- Jumbled deck of cards: 225.6
Tabula Recta
Information cribbed from Aaron Toponce's blog.